Conditional Access System for IPTV
NetUP's Conditional Access System (CAS) encrypts the content for transmission over unprotected channels. The content may be reproduced only by the authorized users. By means of this system, the IPTV provider may control the clients' access to the content, as well as the ensuing financial commitments.
The System is registered in an international organization DVB Project. Conditional Access Identification (CAID) – 0x4AEF.
NetUP CAS/DRM is intended to be used as a component of the NetUP.tv solution. The system can work with different client equipment: classical and Android-based IP set-top boxes, and PC. Depending on the equipment type different encryption algorithms are used (CSA or AES) to optimally utilize the onboard STB hardware resources to decrypt the streams. This decreases the overall IP STB load that is especially critical in case of High Definition video. CSA (Common Scrambling Algorithm), a scrambling algorithm developed in 1994, is today widely used in digital broadcasting. AES (Advanced Encryption Standard) is currently the most popular symmetric-key encryption algorithm.
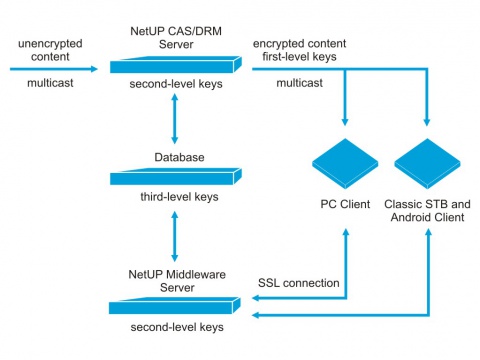
NetUP CAS/DRM workflow
The CAS server accepts content from an IP network to one of its network interfaces, encrypts it, and sends via another interface into an IP network where the IPTV consumers reside.
Once encrypted, the content is sent to an STB client or a PC client. The STB must have the NetUP firmware installed, which accepts and decrypts the content, and also implements the Middleware graphical interface (these functions are not intended to be handed over to a third-party software).
The CAS server interacts closely with the IPTV Middleware to ensure the clients' authentication. The CAS and Middleware servers of one IPTV complex share a common database.